Azure Advanced Threat Protection or Azure ATP is a cloud-based offering to detect and protect your environment from advanced persistent attacks “APT”. This blog post covers:
- Microsoft ATP solutions
- Introduction to Azure ATP
- Comparison between Microsoft ATA and Azure ATP
Microsoft ATP solutions
We live in a world where attacks are becoming very complicated and can be highly targeted. Therefore, normal security solutions based on signature-based filtering and network segmentation are not sufficient to detect and defends against such attacks. Furthermore, a recent study shows that 9 out of 10 CIO believe hybrid cloud is their long-term vision, and that some of their data will remain on-premises.
Since there is a big adoption of the cloud and SaaS applications, it would not make sense to keep relying on traditional on-premise firewalls and network segmentation. Moreover, people are working remotely more than before and they are using a variety of devices. Therefore, security is becoming a nightmare for companies, yet a top priority for every business out there.
Microsoft is responding with their new line of advanced threat protection solutions, to help businesses address this need. They offer a new cloud-base defense in depth model based on three different yet integrated solutions, that work together for better insight and protection. Powered by the Microsoft Intelligent Security Graph ISG, Microsoft definitely has a unique and comprehensive offering, delivered through their E5 licensing model.
Since most malware is delivered through email, Microsoft is offering their Office 365 Advanced Threat Protection solution as part of Office 365 E5. This can be considered the first line of defense. Office 365 ATP detects zero-day attacks using two technologies: Safe Attachments and Safe Links.
Next, is the device or endpoint ATP solution, called Windows Defender ATP. If Windows Defender ATP detects a suspicious file that was delivered through Exchange Online, it will immediately notify Office 365 ATP to prevent further infections.
Finally, if the attacker could compromise a device, then Azure advanced threat protection can help detect lateral movement inside your network. Moreover, Azure advanced threat protection is integrated with Windows Defender ATP for better insight of what is happening inside your network from identity and device perspectives.
 Introduction to Azure ATP
Introduction to Azure ATP
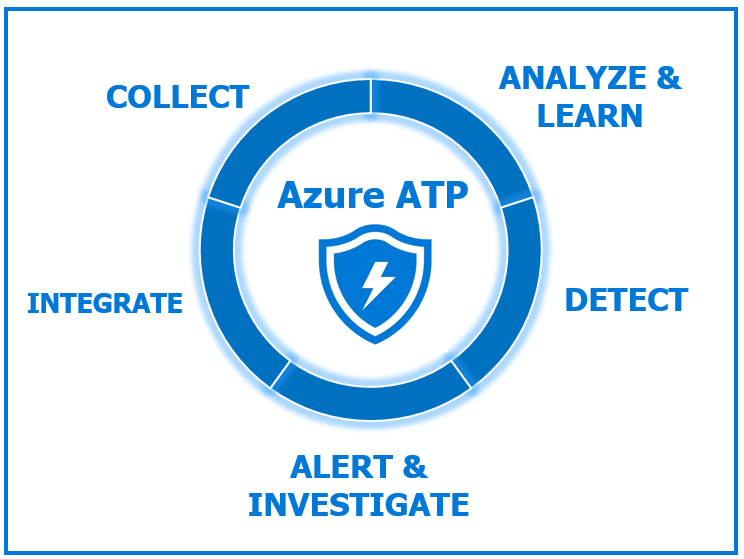
Azure advanced threat protection can help detecting multiple suspicious activities inside the network, and alert on abnormal behaviors after analyzing the normal authentication pattern inside the organization. It integrates well with Windows Defender ATP, and you can move from Azure ATP management portal and Windows Defender ATP portal without loosing context. There are four major phases for Azure ATP:
Collect Phase
Azure advanced threat protection can collect traffic from domain controllers using specialized agent on the domain controller itself, or using a separate server with port mirroring. Moreover, Azure ATP can get logs from SIEM and can receive RADIUS accounting logs. There are other sources of logs that Azure ATP can collect, like Windows event forwarding from your domain controllers.
Analyze and learn phase
Now that the logs are available, Azure ATP starts to learn about each and every entity inside the directory. This can be a user account, computer account or even a group. Azure ATP learns the behavior of each entity based on:
- When each entity usually logs on the network.
- What devices are being used by each entity.
- What resources are accessed by each entity.
Azure advanced threat protection then builds a model that can detect anomalies and abnormal behaviors. So, if Azure ATP sees multiple failed logon attempts by a specific user happening from dozen of devices, it will consider this a suspicious activity.
Detect Phase
Azure advanced threat protection uses two techniques for detection:
- Known suspicious activities: There are predefined activities that Azure ATP knows about and will detect right away.
- Behavioral Analysis: Azure ATP uses machine learning to learn the authentication pattern of each entity inside the network, and for the whole organization. It will then be able to detect any anomalies based on abnormal behaviors and lateral movements. It does that by learning about entities inside the directory, when each entity usually authentications, from which device, and what resources it usually accesses.
Alert and investigate phase
Once a detection is found, Azure ATP can send email to the security teams notifying them about new possible threat. It will also display all alerts in an intuitive attack timeline that provides all the details of the possible attack, and a separate detailed page for each alert.
Comparison between Microsoft ATA and Azure ATP
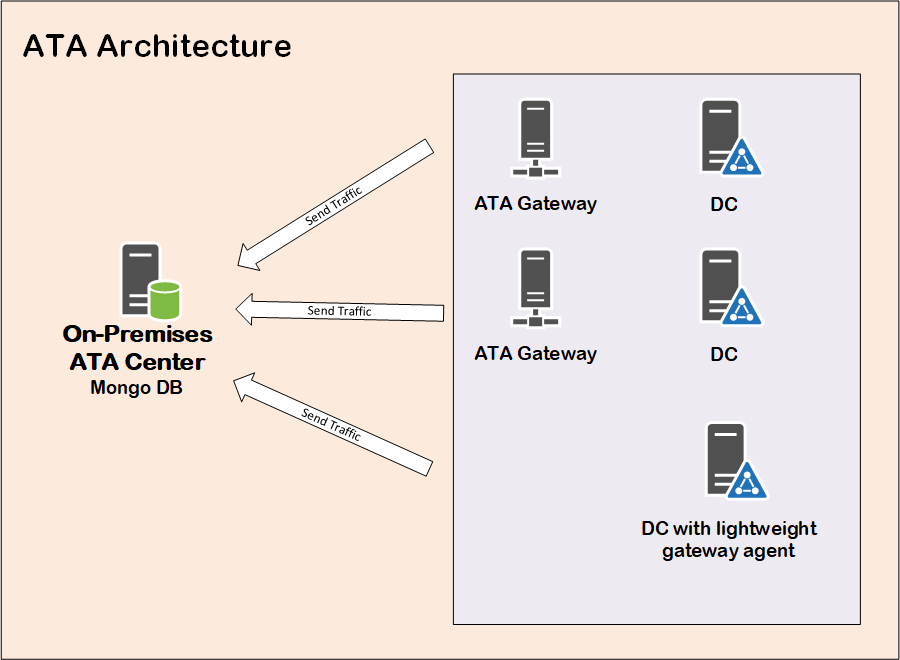
Microsoft launched their Identity based anomaly detection solution years back under the name of Microsoft Advanced Threat Analysis or ATA. By capturing network traffic from domain controllers and collecting logs from other possible sources, Microsoft ATA can detect suspicious activities and analyze abnormal patterns.
Microsoft ATA comes with the need to deploy the ATA Center, which collects and analyzes logs collected from various sources, like domain controllers or SIEM. Therefore, you have to maintain an on-premise server and keep updating it with new releases.
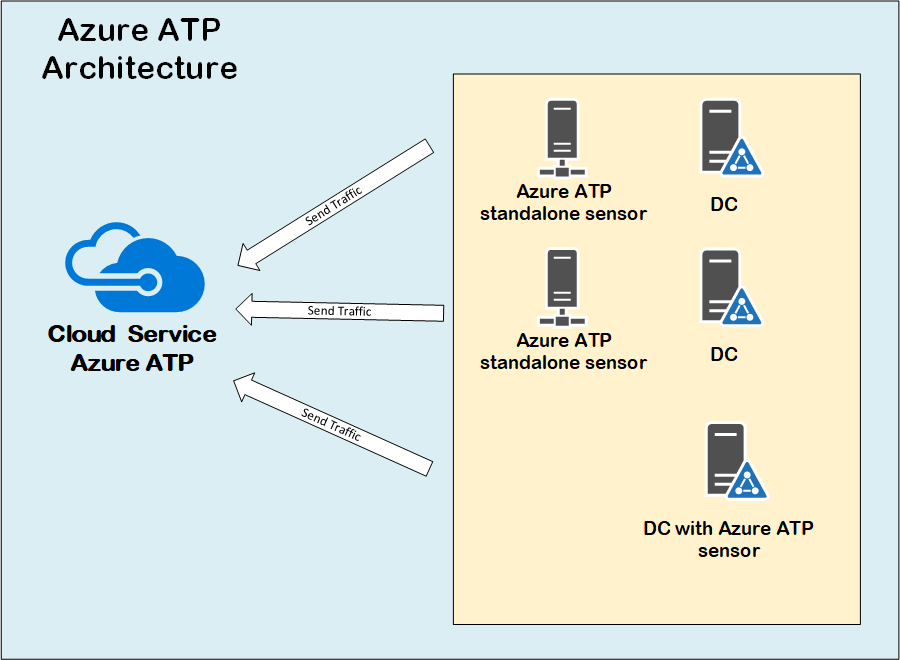
Microsoft decided to offer the ATA center as a cloud service under the name of Azure ATP. Actually, it is more than just offering the ATA center role as a service, as the whole solution is completely re-engineered for better performance, scale and integration with other Microsoft cloud solutions.
Azure ATP is considered the cloud-based evolution of Microsoft ATA, and offers a better integration with other Microsoft ATP solution. It also comes with a lot of the performance improvements for the on-premises agent compared to Microsoft ATA agents. Since Azure ATP is hosted in Azure, it can benefit from the cloud scale and built-in availability that might be hard to have on-premises.
References
- Microsoft documentation reference for Azure ATP.
- Azure ATP deep dive and architecture blog posts.

 Introduction to Azure ATP
Introduction to Azure ATP